
Is Cloud Storage a Safe Option for Your Data?
November 2, 2024
VMware Issues Critical Updates for vCenter Server Flaw
November 7, 2024Cybersecurity is an essential framework designed to protect information systems, networks, and data from cyber threats. Organizations are increasingly implementing a layered approach to cybersecurity to address the complex landscape of cyber risks. Known as the “7 Layers of Cybersecurity,” this model provides a comprehensive strategy by addressing different levels within an organization’s IT infrastructure. Below, we dive into each of these seven layers and how they contribute to a resilient cybersecurity strategy.
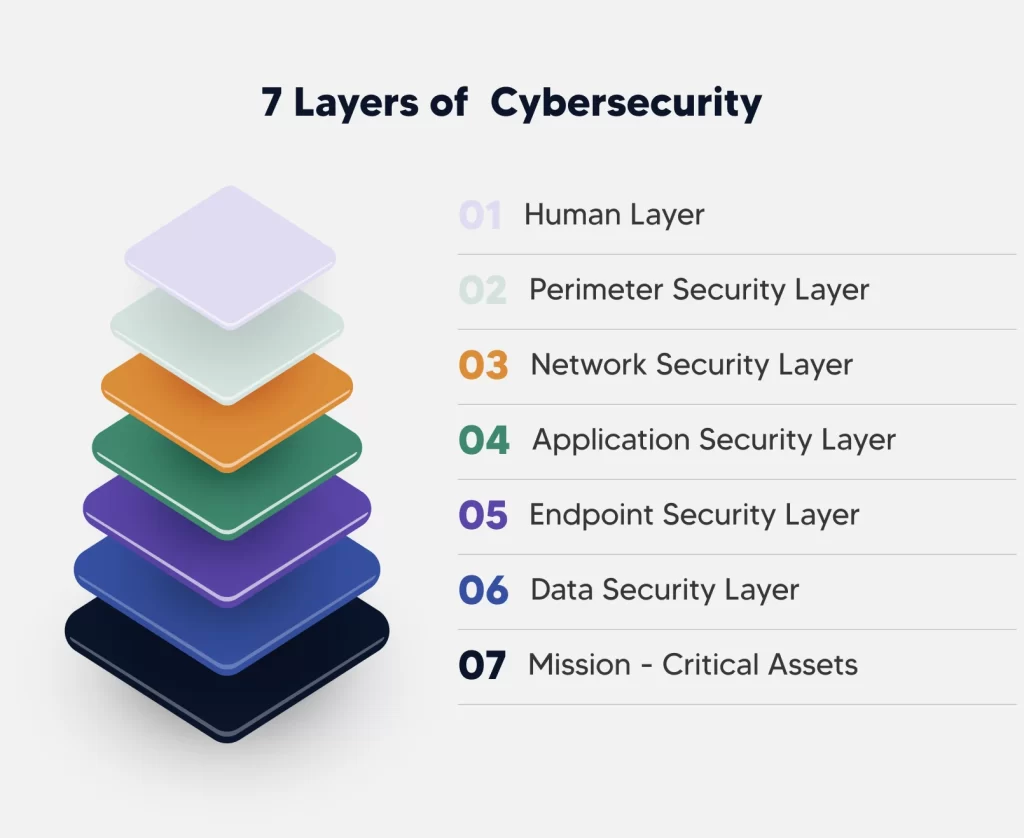
1. Human Layer
People are often considered the first line of defense against cyber threats, but they can also be the weakest link if not properly trained. This layer focuses on educating employees, stakeholders, and end-users about cybersecurity practices to reduce the risk of human error. Training typically includes phishing awareness, password management, recognizing suspicious activities, and adherence to organizational policies. Organizations can conduct regular security awareness training sessions, run phishing simulations, and set clear guidelines on handling sensitive data. Empowering users to recognize potential threats is essential to preventing breaches from accidental clicks or incorrect decisions.
2. Perimeter Security
The perimeter layer is the first technical layer that serves as a boundary between an organization’s network and the external internet. It includes firewalls, intrusion detection and prevention systems (IDPS), and VPNs. Firewalls act as a gatekeeper, inspecting incoming and outgoing traffic based on predefined security rules. IDPS monitors network traffic to detect and respond to abnormal patterns that may indicate an attack. VPNs are essential for secure remote access, creating encrypted tunnels between users and the corporate network. Perimeter security is crucial for safeguarding the network from unauthorized access and reducing the risk of infiltration by external threats.
3. Network Security
While perimeter security acts as the outer layer, network security focuses on the internal protection of the organization’s network. It includes a range of technologies like network segmentation, VLANs (Virtual Local Area Networks), and secure network protocols to limit unauthorized access and contain potential breaches. For example, network segmentation divides the network into smaller segments, limiting access to sensitive areas and reducing the spread of malware. Advanced network security systems also use anomaly detection to identify irregular traffic patterns. This layer ensures that the organization’s internal network is robust and capable of detecting and isolating threats within the system.
4. Endpoint Security
Endpoints, such as computers, mobile devices, and servers, are common entry points for cyberattacks. Endpoint security focuses on securing these devices from threats like malware, ransomware, and unauthorized access. Tools such as antivirus software, endpoint detection and response (EDR) systems, and mobile device management (MDM) systems help protect endpoints. EDR solutions go beyond traditional antivirus by continuously monitoring endpoints and providing real-time threat detection and response. Since endpoints are widely dispersed across the organization, they are prime targets for attackers, making this layer essential for preventing intrusions.
5. Application Security
Application security is a layer that focuses on securing software applications, both those developed in-house and third-party applications used by the organization. This layer involves practices like secure coding, code review, vulnerability scanning, and the use of application firewalls. By applying these measures, organizations can prevent attacks that exploit software vulnerabilities, such as SQL injection, cross-site scripting (XSS), and buffer overflows. For applications in development, secure coding standards and regular testing are necessary to identify and fix vulnerabilities before deployment. Securing applications is vital since compromised applications can serve as gateways for attackers to access sensitive data.
6. Data Security
Data is at the core of an organization, and its protection is crucial. Data security focuses on securing information wherever it is stored, transmitted, or processed. Encryption, access controls, data masking, and data loss prevention (DLP) tools are common techniques used in this layer. Encryption ensures that even if data is intercepted, it cannot be read by unauthorized users. DLP systems monitor data movement and prevent unauthorized sharing, while data masking conceals sensitive information in non-production environments. Data security is essential for compliance with regulations and for maintaining the integrity and confidentiality of an organization’s data.
7. Mission Critical Assets
Mission-critical assets are the most valuable resources within an organization, such as intellectual property, customer data, and operational systems essential for business continuity. Securing these assets requires the highest level of protection, often combining elements from other cybersecurity layers. This layer includes risk assessment, regular audits, and disaster recovery planning. Identifying mission-critical assets allows organizations to prioritize their protection and allocate resources effectively. Often, this layer also involves implementing backup and redundancy measures to ensure that operations can continue in case of an attack. Protecting mission-critical assets is the final line of defense and helps to minimize the impact of any successful breach on the organization’s core functions.
By implementing these seven layers of cybersecurity, organizations can create a comprehensive defense strategy, protecting their digital assets, minimizing risks, and preparing for potential cyber incidents. Each layer plays a crucial role, addressing specific aspects of security and working together to create a multi-layered defense that is both proactive and reactive to evolving cyber threats.





