
Cisco Investigates Major Data Breach: Sensitive Developer Data at Risk!
October 17, 2024
Understanding Ransomware: What It Is and How to Protect Yourself
October 17, 2024In today’s digital landscape, email security has never been more crucial. As cyber threats become increasingly sophisticated, attackers continuously evolve their techniques to bypass traditional security measures. One alarming trend is the rise of image-based fraud, a tactic that poses significant challenges for detection and prevention.
The Challenge of Image-Based Fraud
Have you ever received an email from a service you don’t remember signing up for? Or perhaps an email that seems legitimate but feels slightly off? Information overload is a common strategy employed by attackers to catch their victims off guard. As traditional security controls improve, threat actors pivot their methods, often trying to move transactions off corporate monitored networks. This shift has led to a surge in telephone-oriented attack delivery (TOAD) attacks and other types of image-based fraud.
These fraudulent emails often lack actual text, making it difficult for traditional anti-spam technologies to identify them. Despite clear red flags—such as brand abuse—these emails can slip through conventional defenses. The challenge is magnified by the fact that security analysts may recognize a particular image as fraudulent, yet traditional detection methods like block rules or regular expressions struggle to identify them effectively.
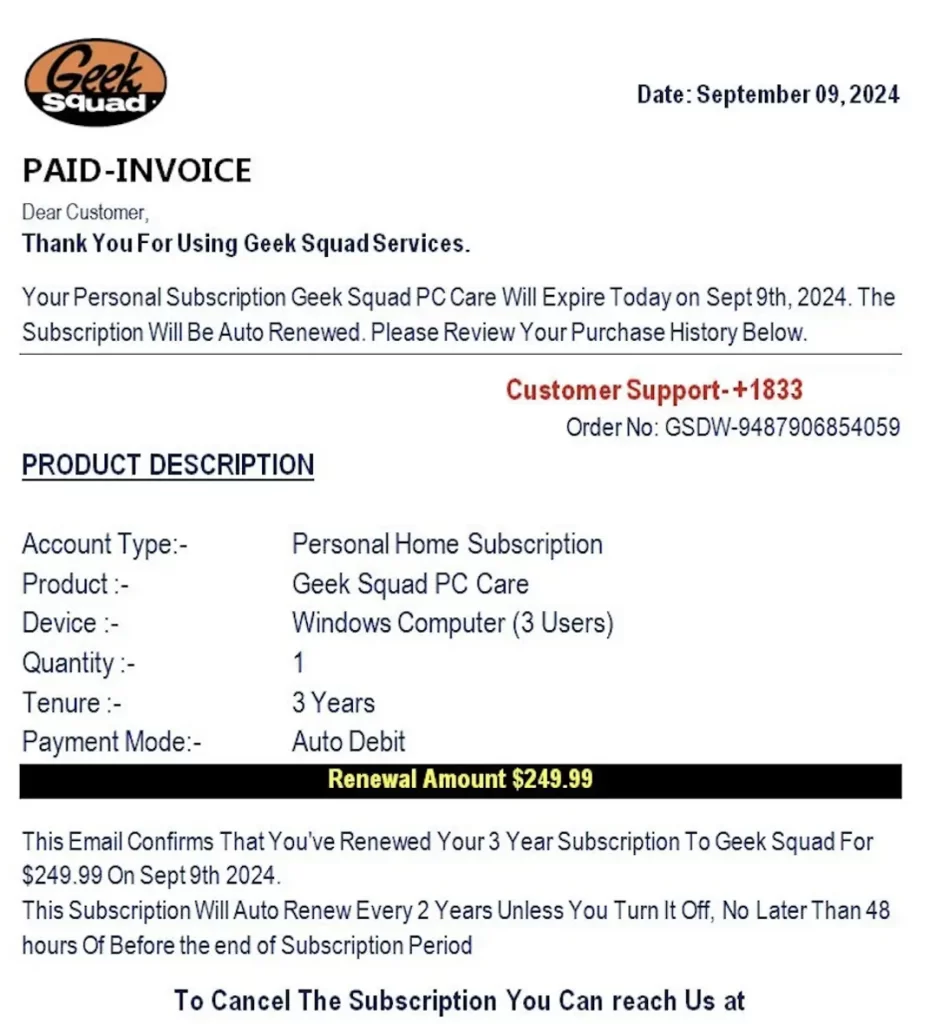
Cisco’s Innovative Approach to Email Security
At Cisco, we are committed to advancing email security through the use of Machine Learning (ML) and Deep Learning (DL) models. These cutting-edge technologies allow us to understand the intentions behind messages and ascertain the true sender. Our approach transcends simple analysis, enabling us to comprehend the calls to action embedded within email content.
Advanced Detection Techniques
Our data science team employs Optical Character Recognition (OCR) detection that utilizes Long Short-Term Memory (LSTM) neural networks for content extraction. This is particularly important in the realm of email security, which must contend with the scale of processing millions of images, URLs, files, QR codes, and other objects daily. By harnessing new artificial intelligence methodologies, we can implement heuristics to determine which images merit further analysis.

This selective approach enables us to process and interpret signals and calls to action more effectively. The insights gleaned from this valuable data enhance our detection engines, allowing for a more nuanced assessment of intent behind the emails we analyze.
In an era where email fraud continues to evolve, leveraging AI technologies offers a robust solution to combat these emerging threats, ensuring a safer digital communication landscape for all.





