
Hackers Exploit ChatGPT for Malware Creation and Cyberattacks
October 14, 2024
Jetpack Plugin for WordPress Fixes Critical Security Flaw Impacting 27 Million Websites
October 15, 2024Phishing attacks are one of the most prevalent and dangerous threats in the realm of cybersecurity. These malicious attempts aim to deceive individuals into providing sensitive information, such as passwords, credit card numbers, or personal identification, by masquerading as a trustworthy entity. As technology advances, so do the tactics employed by cybercriminals, making awareness and prevention crucial for individuals and organizations alike.
How Phishing Works
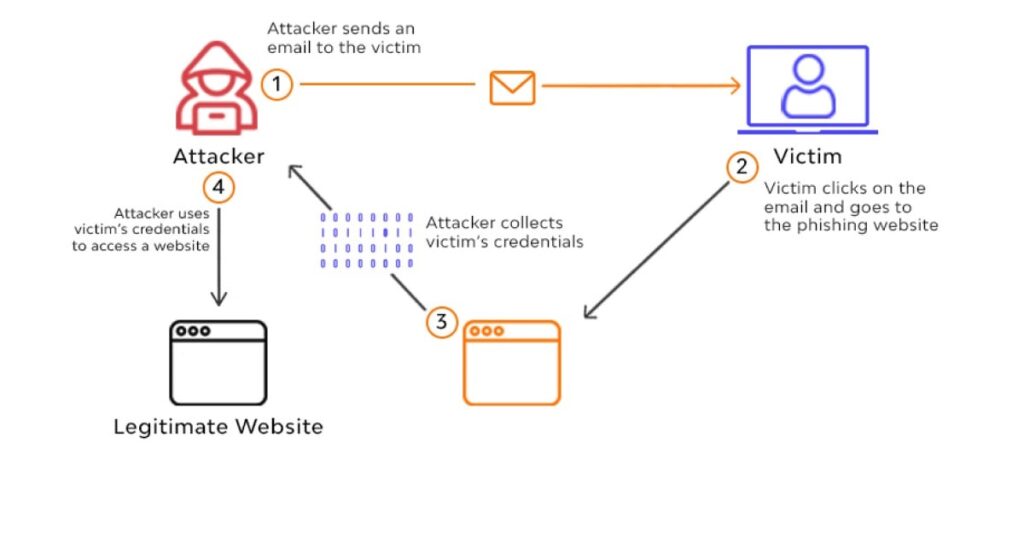
Phishing typically occurs through emails, messages, or websites that appear legitimate. For instance, a user might receive an email that looks like it’s from their bank, prompting them to click on a link to verify their account details. Once the user clicks on the link, they are directed to a counterfeit website that closely resembles the official site. If the user enters their credentials, they unknowingly hand over their sensitive information to the attackers.
The Rise of Spear Phishing
One of the most alarming trends in phishing is the rise of “spear phishing.” Unlike traditional phishing attacks, which are generally sent to large groups, spear phishing targets specific individuals or organizations. Attackers often conduct extensive research to tailor their messages, making them appear highly credible. This personalized approach significantly increases the likelihood of success, as victims may let their guard down when they believe the communication is from a known source.
Other Forms of Phishing
Phishing attacks can also manifest in various forms, including vishing (voice phishing) and smishing (SMS phishing). Vishing involves phone calls from scammers pretending to be representatives from legitimate organizations, while smishing utilizes text messages to lure victims into clicking malicious links. These methods exploit the same psychological tactics as traditional phishing, relying on urgency, fear, or curiosity to prompt immediate action from the victim.
Prevention Strategies
To combat phishing attacks, individuals and organizations must adopt a proactive cybersecurity strategy. Education is vital; users should be trained to recognize suspicious emails and messages, scrutinizing the sender’s address and looking for grammatical errors or inconsistencies. Implementing multi-factor authentication (MFA) adds an extra layer of security, making it more difficult for attackers to gain access even if they acquire login credentials.
Additionally, utilizing anti-phishing tools and regularly updating software can help protect against these threats. Organizations should also maintain a robust incident response plan to address potential breaches swiftly.





