
How to Secure Your MacOS X Operating System Against Unauthorized Access
October 30, 2024
Microsoft Delays Release of Windows Copilot+ Recall Feature Due to Privacy Concerns
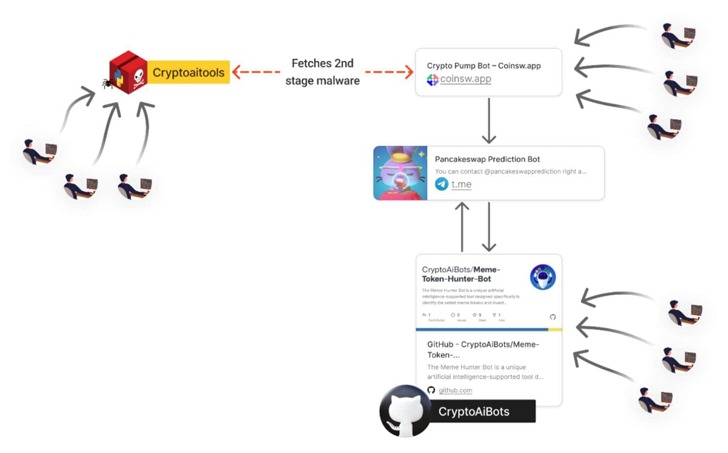
November 1, 2024Cybersecurity experts have uncovered a malicious Python package, “CryptoAITools,” which poses as a cryptocurrency trading tool but is actually designed to steal sensitive data and drain assets from victims’ crypto wallets. This package, distributed via the Python Package Index (PyPI) and fake GitHub repositories, was downloaded over 1,300 times before PyPI removed it.
According to Checkmarx, the malware activates automatically upon installation, affecting both Windows and macOS systems. A misleading graphical user interface (GUI) was crafted to distract users while the malware operates covertly in the background. Through injected code in its __init__.py file, the package identifies the operating system to execute a specific version of the malware accordingly.
A notable feature of this malware is its multi-stage infection, initiated by helper code that downloads and executes additional payloads. These payloads are sourced from a fake site, “coinsw[.]app,” which pretends to offer a legitimate cryptocurrency trading bot service, enhancing the malware’s chances of going undetected.
The malware gathers sensitive data, targeting crypto wallets (such as Bitcoin, Ethereum, Exodus, Atomic, and Electrum), saved passwords, browsing history, SSH keys, and financial documents stored in directories like Downloads, Documents, and Desktop. On macOS, it also collects data from Apple Notes and Stickies apps. Once collected, the data is uploaded to gofile[.]io, after which local copies are deleted.
Checkmarx also discovered that the same malware was distributed through a GitHub repository called “Meme Token Hunter Bot,” which claims to be an AI-driven trading bot for meme tokens on the Solana network. The repository, promoted via a Telegram channel that offers subscriptions and technical support, has been forked and starred multiple times.
This campaign underscores the wide reach of the attack, as the malware can infect users who clone or directly download the code from GitHub. By targeting multiple platforms, the attackers can exploit a larger user base, potentially affecting those who may trust one platform over another.





