Roundcube Webmail Vulnerability Exploited by Hackers
October 21, 2024
The 10 Biggest Cybersecurity Trends in 2024 You Need to Prepare For
October 22, 2024A recent study conducted by ETH Zurich cybersecurity researchers has revealed significant cryptographic vulnerabilities in several prominent end-to-end encrypted (E2EE) cloud storage platforms, potentially compromising sensitive user data. The researchers, Jonas Hofmann and Kien Tuong Truong, highlighted that these flaws could allow a malicious server to intercept files, modify their content, or gain access to plaintext data. These findings are alarming given the widespread trust in E2EE services to protect user confidentiality.
Affected Providers
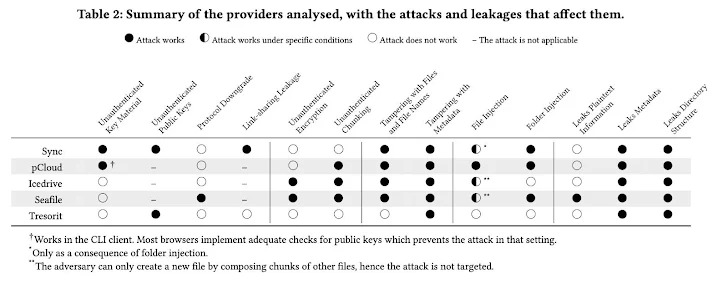
The research examined five major E2EE cloud storage providers: Sync, pCloud, Icedrive, Seafile, and Tresorit. Each platform exhibited vulnerabilities that could be exploited by attackers controlling a compromised server. Here’s a breakdown of the major flaws:
- Sync: Attackers could breach file confidentiality, inject malicious files, and tamper with stored content.
- pCloud: Similar vulnerabilities to Sync, with potential for data tampering and file injection.
- Seafile: Vulnerable to brute-force attacks on user passwords, as well as file tampering and injection.
- Icedrive: File integrity issues were found, with the possibility of file content modification and injection.
- Tresorit: Attackers could present unauthenticated keys when sharing files and manipulate metadata.
Common Attack Vectors
The flaws fall into ten broad categories, affecting both file data and metadata. Key issues include:
- Lack of authentication for user key material (Sync, pCloud)
- Unauthenticated public keys (Sync, Tresorit)
- Protocol downgrade vulnerabilities (Seafile)
- Tampering with file names, locations, and metadata (affecting all providers)
- The injection of rogue files or folders into user storage (Sync, pCloud)
Notably, some attacks are easily executable and don’t require advanced cryptographic expertise, making them accessible to a broader range of malicious actors.
Provider Responses
- Icedrive has not addressed the issues, maintaining that their zero-knowledge encryption is secure, but they acknowledged the research findings.
- Sync acknowledged the vulnerabilities and stated that fixes are underway, with some issues already resolved.
- Tresorit highlighted that while their system was largely unaffected, they plan further enhancements, including public key fingerprint verification in 2025.
- Seafile introduced a version update to mitigate protocol downgrade attacks and added a statement in their manual clarifying limitations regarding data integrity.
Industry Impact
The findings underscore critical design flaws in current E2EE cloud storage implementations, highlighting that many services do not fully protect against adversarial actions by compromised servers. The research team emphasized the need for stronger cryptographic protocols and stricter authentication measures to prevent such vulnerabilities in the future.
While some platforms have taken steps to address the issues, these findings call for a broader industry shift toward more robust security practices.





