
4 Million WordPress sites Are at Risk Due to a Flaw
November 16, 2024
Amazon Data Breach Tied to MOVEit Hack
November 18, 2024Cybersecurity researchers have uncovered a new remote access trojan (RAT) and information-stealing malware, dubbed WezRat, employed by Iranian state-sponsored hackers. The malware facilitates reconnaissance on compromised systems and allows attackers to execute malicious commands.
According to cybersecurity firm Check Point, WezRat has been active since at least September 1, 2023, based on samples found on the VirusTotal platform. The malware’s capabilities include executing commands, capturing screenshots, uploading files, logging keystrokes, and stealing clipboard data and browser cookies. It said in a technical report. Some of its advanced functions are delivered through additional modules downloaded from a command-and-control (C&C) server, making the primary backdoor appear less suspicious.
Origins and Attribution
WezRat is attributed to Cotton Sandstorm, an Iranian hacking group also known by aliases such as Emennet Pasargad and Aria Sepehr Ayandehsazan (ASA). The malware was first reported in detail last month by U.S. and Israeli cybersecurity agencies, which described it as an exploitation tool for gathering endpoint information and executing remote commands.
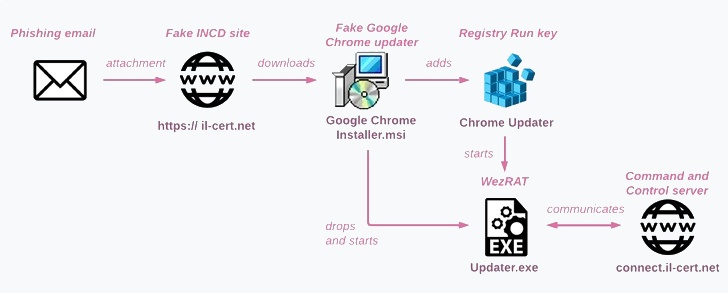
Attack Methodology
The attack chain involves trojanized Google Chrome installers disguised as legitimate updates. These installers, named “Google Chrome Installer.msi,” install Chrome but also execute a malicious binary named “Updater.exe” (referred to internally as “bd.exe”). This executable collects system information and establishes communication with a C&C server (“connect.il-cert[.]net”), awaiting further instructions.
On October 21, 2024, phishing emails impersonating the Israeli National Cyber Directorate (INCD) were sent to multiple Israeli organizations. The emails, originating from “alert@il-cert[.]net,” urged recipients to install a fake Chrome security update. When executed, the backdoor connects to the C&C server with parameters including a “password” argument that ensures proper execution. An incorrect password causes the malware to malfunction or crash.
Advanced Features
WezRat supports various malicious functions, including:
- Configuring fallback C&C servers.
- Uploading and downloading files.
- Capturing screenshots and logging keystrokes.
- Stealing clipboard content and browser cookies.
- Executing commands via cmd.exe.
Earlier versions of WezRat featured hard-coded C&C addresses and lacked the password-based execution safeguard. Over time, the malware has evolved, gaining enhanced features like modular commands for specific tasks.
Development Insights
Check Point’s analysis suggests that at least two separate teams are involved in WezRat’s development and operational deployment. The malware’s continual refinement points to a significant investment in creating a versatile and stealthy cyber-espionage tool.
Broader Implications
WezRat’s use underscores the broader ambitions of Emennet Pasargad, which targets organizations in the U.S., Europe, and the Middle East. These attacks threaten not only Iran’s direct adversaries but also entities with potential influence on the country’s domestic or international narratives.
Check Point concluded that the sophisticated design and deployment of WezRat reflect a dedicated effort to maintain a highly adaptable tool for cyber espionage and intelligence gathering.





