
Balada Injector Malware: Over 7,100 WordPress Sites Infected
January 16, 2024
Critical Cisco Vulnerability Exposes Unified Comms Systems to Remote Takeover
January 29, 2024Cybersecurity researchers have sounded the alarm about a new invoice phishing campaign targeting individuals and businesses. The campaign, attributed to the financially motivated cybercrime group TA866, leverages a devious multi-step infection chain to deliver WasabiSeed and Screenshotter malware.
The campaign was observed earlier this month and was blocked by Proofpoint on January 11, 2024. It involved sending thousands of invoice-themed emails targeting North America bearing decoy PDF files.
“The attack begins with emails containing seemingly legitimate invoices, embedded with OneDrive links” the enterprise security firm said.
Clicking on the link triggers the first step: the download of a decoy PDF file. This document, however, doesn't hold the invoice but instead contains another hidden URL disguised within its code. Once clicked, this second URL activates WasabiSeed, a credential-stealing Trojan targeting email clients, online banking portals, and cryptocurrency wallets. WasabiSeed then downloads its partner-in-crime, Screenshotter.
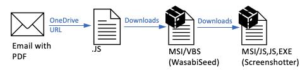
This malware duo works synergistically. While WasabiSeed furtively gathers login credentials and financial data, Screenshotter silently captures screenshots of the victim's desktop at regular intervals. This potent combination allows attackers to not only pilfer sensitive information but also potentially glean visual clues to access additional accounts or sensitive documents displayed on the screen.
This campaign highlights the escalating sophistication of phishing tactics. TA866's targeted approach, focusing on high-value individuals and businesses in sectors like finance and manufacturing, coupled with their adoption of novel malware like WasabiSeed and Screenshotter, demonstrates their efforts to bypass traditional security measures.
There also mentions the growing threat of other specialized phishing tools like DarkGate and Agent Tesla, often targeting specific industries like healthcare and critical infrastructure.
The rise of such sophisticated invoice phishing campaigns underscores the imperative for heightened cybersecurity vigilance. Users and organizations must remain wary of unsolicited emails, particularly those containing embedded links or attachments. Verifying sender legitimacy, refraining from clicking on suspicious links, and maintaining robust security practices are crucial steps in mitigating the risk of falling victim to these attacks.
By staying informed about evolving phishing tactics and adopting proactive security measures, individuals and businesses can safeguard themselves from the financial and reputational damage caused by these cyberattacks.





